This post is part of a series explaining our publicly available resources for user research. The previous installment covered how to write screeners to recruit participants. This week, we discuss how to get model releases to share photos from user studies.
One approach among many
At Simply Secure, we strive to balance study participants' privacy with building empathy in an audience of developers, policymakers, and designers by sharing study photos and stories. Meanwhile, many startups have used exploitative and borderline unethical user testing methods that make extensive use of behavior tracking. Privacy-preserving technology is evolving. Now is the time to develop best practices that both enable meaningful data collection on user experience and respect users' privacy. There are many ethical ways to handle data collection, and the following is an approach we used in one of our studies.
We recently conducted a user study about participants' experience with surveillance and the strategies they use to preserve their privacy. There's an inherent paradox in recording a conversation about surveillance, and to acknowledge this, we decided that handwritten notes were sufficient to capture attitudes towards surveillance and personal strategies to get around it. Instead of recording audio or video during the interviews, our researchers only took notes on paper. In situations where anonymity is critical to our participants' safety, we asked them to tell us what they'd like to be called rather than collecting their names and contact details.
Why take photographs?
As a designer, I'm a visual person and find photos to be a powerful note-taking tool and memory aid. When I look at a photo from a user study from 10 years ago, I can remember specific details of the conversation and insights from the study even though I haven't interacted with the participant since then. Not only are photos useful to designers as memory aids, they are powerful in inviting an audience into a user's story. They help the audience internalize learnings from a study.
Photography is always an opt-in process
Despite its benefits as a mnemonic, participants should never feel pressured to have their photo taken. At the beginning of Simply Secure interviews, participants are given a Participant's Bill of Rights that outlines consent procedures, including the ability to refuse any questions, quit and still be compensated, and refuse photography.
In a winter 2015 study, we helped participants understand how the photos could be used by showing them photos from the Humans of New York's (HONY) Instagram feed. HONY combines photos of people in public space, with descriptions of what they are doing or thinking. These powerful stories are akin to bite-sized doses of user research. We used HONY's feed to demonstrate how we might share their stories and personally identifiable photos on the public web.
In the final 5-10 minutes of our session, we asked if people were comfortable posing for photos. Doing this at the end is beneficial because participants have a clearer idea of who we are and are conscious of the stories they've shared. Participants could choose from three types of photographic participation:
- No photography
- Being photographed in a personally meaningful but non-identifiable way (such as their shoes or purses)
- Being photographed in an identifiable way
What a model release means
Our default is to avoid collecting personally-identifiable information, but in instances where we do, we ask study participants to sign our model release. This step is central to how Simply Secure balances building audience empathy and protecting participants' privacy.
There are clear concerns that modeling is exploitative and harmful to people, and the choice of using a model release—and calling it a "model release"—is an intentional one.
An important ethical consideration of model releases is that models lose control of their images and cannot choose how their narratives will be paired with them. When using HONY as an example, we showed a photo of a man who talked about the aftermath of his domestic violence conviction. By talking through this provocative example, we were confident that our participants appreciated how hard it can be to get a nuanced picture of people's stories.
We explained that although we had no plans to put the images on Instagram, we would like to share them on our blog and in presentations. That's a much smaller audience than popular Instagram feeds, but there are implications of sharing photos anywhere on the open web.
Some examples
Of the 12 participants in our study, three signed model releases, five agreed to non-personally-identifiable photos, and four did not want to be photographed. We took photos with an iPhone, and everyone was offered a chance to review them. Rather than candid shots, we took staged photos to portray the participants as powerful, positive people. After some minor photo filtering and cropping, we sent copies of the photos to participants who signed model releases to get their approval for public use.
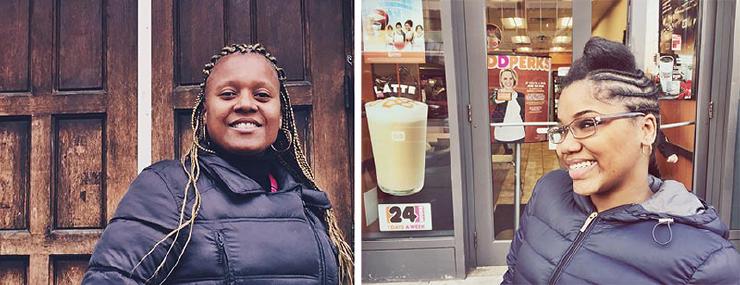
Study participants who signed model releases for sharing photos.

Non-personally identifiable photos, taken with verbal consent, but not a signed model release.
We're still learning
Since our study was about surveillance and personal strategies to preserve privacy, we asked participants to show us examples of how they use their phones. With their permission, we photographed their phones. We blurred out their names and personal information before sharing any photos publicly, but photos with homescreens, photos, and wallpaper required extra sensitivity.
Consider the photos below. One of the participants had a photo of herself as the wallpaper. She was comfortable sharing the photo and signed a model release. But what should we do if her wallpaper were a photo of another private individual? How should we approach photography when the wallpaper is a photo of a child? Complicating matters, does it change things if the participant is the parent versus a relative of the child?
Participants' phones. Photos shared by consent with identifiable text blurred.
We are still learning at Simply Secure, and we believe that a human-centered approach should be a best practice in developing privacy-preserving software. We welcome discussion about best practices for ethical research.
Tell us what you think of how a background image of other private individuals fits into personally identifiable information. If you are a researcher and want to join the research dialogue on our Slack channel, email [email protected].