- With support from the Open Technology Fund, we supported Mobile Surveillance Monitor with human-centered research and design.
- This new tool fills a critical gap in providing researchers and everyday users access to real data in a digestible form on surveillance threats.
- The user research phase was critical in challenging assumptions, building a tool that can be trusted, and understanding which users the tool can best serve. We pursued a phased design process to address questions raised in the research.
Surveillance on mobile devices is rampant globally, yet security researchers and everyday users alike struggle to access real data on surveillance threats and where they’re coming from. With support from the Open Technology Fund (OTF), we helped the brand new platform Mobile Surveillance Monitor (MSM) fill this gap by providing research and design support. This new tool is both a public resource that tracks mobile threats on a map-based dashboard, and a workbook which provides researchers with detailed charts and investigation tools to uncover new details about multiple types of threats.
Through our collaboration with MSM, we were able to dig deep into the UX of surveillance resources, an arena that often does not incorporate human-centered design practices. We learned that the design of these tools is a big responsibility, relying upon deep trust and user empowerment through education.
We began our work with MSM with desk research to develop a foundational understanding of current needs and trends in surveillance threat software. We then completed five anonymous, in-depth user interviews with cybersecurity experts, advocates, researchers, human rights workers, and government contractors, who were asked about their experiences being under the threat of surveillance, surveillance mitigation, and their impressions of MSM as a resource.
In the intervening time, we contracted a brand designer who developed an identity for MSM that moved away from the dark, ominous, hacker-style common to cybersecurity tools to a more practical and approachable look and feel. After synthesizing the user research findings, we began applying the brand work and the research findings to a first version of the MSM dashboard in partnership with ESRi, a mapping software provider. Finally, after development was complete, we did four user tests to understand some potential users’ perceptions of the site and its usability.
We learned many things throughout this process, but a few key learnings arose:
- OSINT tools that are off-the-shelf, free, available for individual use, and not connected to an institution or organization are relatively rare and/or unreliable. They are even less often informed by a broad and inclusive user-centered design process that does not ‘center’ a ‘security expert’ type of user.
- Designing for surveillance intelligence is delicate, complex, and a lot of responsibility. Developing personas and scenarios of use is critical, and only one part of a larger conversation around safety and threat modeling.
- The users of surveillance security tools are broad and unexpected in some cases. They are not always the ‘tech savvy’ ‘security geeks’ and often are people doing high-risk human rights work with very little time, focus and energy to spend on ensuring safety from surveillance threats. If they are interested, the tools and practices often exclude them through jargon and assumed background knowledge which can feel alienating.
Working on MSM challenged our assumptions and pushed us to get creative to responsibly serve more users over time.
Focusing on the learnings of our research and early design process, we hope that our insights can help others in our ecosystems think through complex challenges around surveillance intelligence and design. Including a thorough research and design process in the development of MSM proved to be critical in a number of ways, most notably because it tested and challenged many of our own assumptions about user needs.
Far before we started designing for MSM, our interviewees urged caution. They emphasized that security tools must be aware of their potential impacts on users, including: giving users a false sense of security, the possibility of users applying intelligence data to their own circumstances misguidedly, eliciting fear without opportunity for action, and eliciting unnecessary fear and/or confusion. Insights from people who have been deeply engaged with surveillance threats from many angles helped us to understand the gravity of designing a security tool and being precise about the intended audience.
That insight was also developed by the most consistent finding from our research: surveillance data is only as good as the threat model it is paired with. Our interviewees shared that a lot of privacy and security guidance assumes too much: they give a lot of advice that doesn’t apply to people’s lives or address the concerns they have. One participant shared: “When people ask what the secure/safe way is to do things - the answer is always: it depends.” These insights ultimately helped us to frame suggestions around MSM’s educational offerings to users, and how critical it is for surveillance data to have appropriate context.
Through our user interviews and other research, we moved toward design and recommendations for MSM with a sense of responsibility and excitement. A critical part of that process was fleshing out user personas to better understand who MSM will serve now, and who else it might be able to serve in the future. We found that the first version of MSM principally serves what we named researcher/academic persona. The researcher/academic uses MSM to study mobile surveillance and form questions about trends to more deeply investigate the factors surrounding them. Our research suggested that MSM also serves what we called the Independent persona – those of mid-tech proficiency, like a journalist or advocate without significant institutional backing – as long as MSM added content and resources to help contextualize the threat intelligence (Which it did!).
As significantly, we found that in order to properly serve the low tech/high risk persona, the platform would need more intensive investment in the content and educational aspects of MSM, with more research and threat modeling on specific targeted groups that would use it. We have plans to continue our work with Gary Miller of Mobile Intelligence Alliance this Fall to explore options for more resourcing and education on MSM for precisely this purpose.
A phased design process proved critical to addressing user needs
We are very proud of MSM’s launch and believe it is a powerful resource for users to explore mobile security threats. We are also committed to those who shared their expertise with us for this project and to sharing our learnings with our community, because, as we learned, it is difficult to design for security tools considering all of the factors that affect user experience!
In the interest of exploring the UX of security tools as a community, we’re sharing an abridged version of our initial phased design proposal that accompanied our user research findings. This is one way that researchers and designers can both advocate for user needs within the parameters of a program or website and offer ideas and solutions to serve more users in the future. MIA and MSM have been wonderful partners, and we’re lucky to already be working toward implementing updated versions of some of these ideas to MSM.
Below is a brief description of those the design phases we hypothesized in our user research synthesis:
Phase 1: A tool for researchers
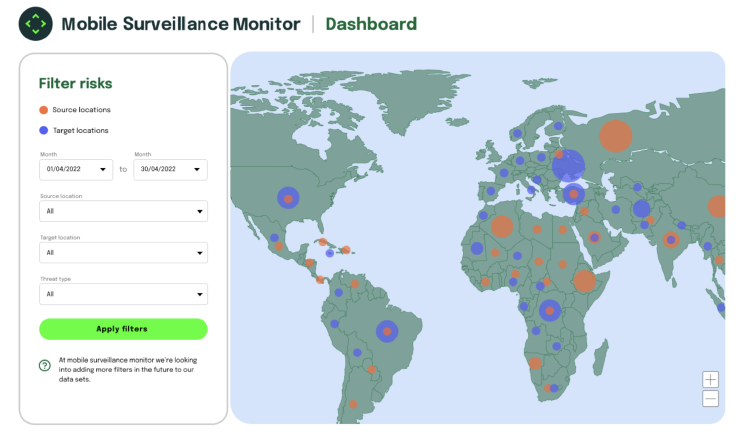
- Purpose: MSM enables researchers to confirm hypotheses and perform geographic and temporal analyses.
- Design priorities: A streamlined, clean, and easily usable dashboard interface (Figure 1). Begin to build infrastructure into the dashboard that can support additional content and educational tools over time (Figure 2). These modules can be flexible, and could be fed by datasets, or could be set up as iFrames with HTML/CSS.
- This design was largely implemented in the live version of the MSM dashboard.
Phase 1 Design
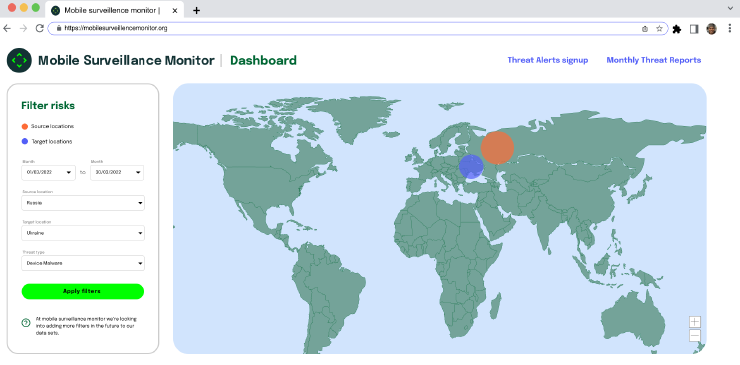
Phase 2: A tool for those concerned about their surveillance risk
- Purpose: Researchers can make increasingly specific searches and associations on the dashboard. Concerned users can filter the dashboard for their location/device type, building a case file for their own protection, and learn about 1) their risk and 2) what they can do about it.
- Design priorities: curate resources for different types of threats, including how people can begin to a develop a threat modeling system for themself or their community. Include definitions / glossary of terms.
Phase 2 Design
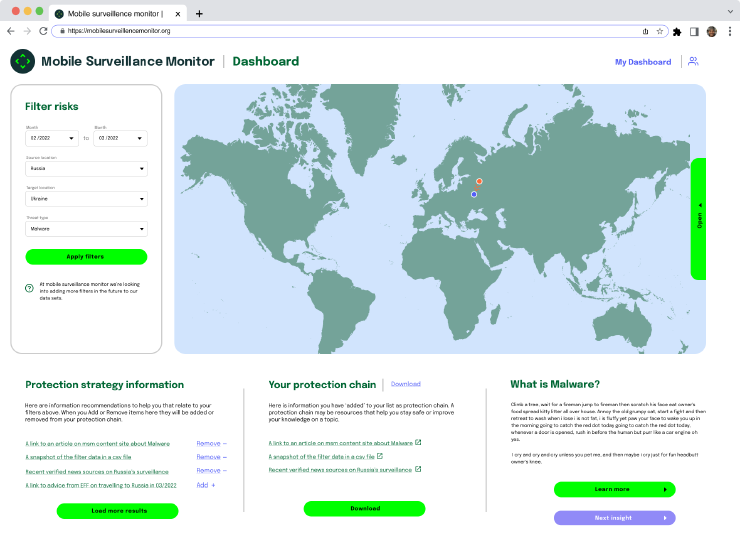
Phase 3: Enable trusted users to contribute resources and data.
- Purpose: Our research showed that surveillance intel is most useful if it is vouched for by a trusted source. This version of the MSM dashboard allows users to save and share their dashboards, and comment on different pieces of data to share their insights. MSM allows “power users” to contribute to the platform to improve its trustworthiness.
- Design priorities: “Power users” can log-in and contribute safety resources, region-specific suggestions, and comment on / report back on experiences they’ve had to help bolster the threat modeling work that the data doesn’t provide on its own.
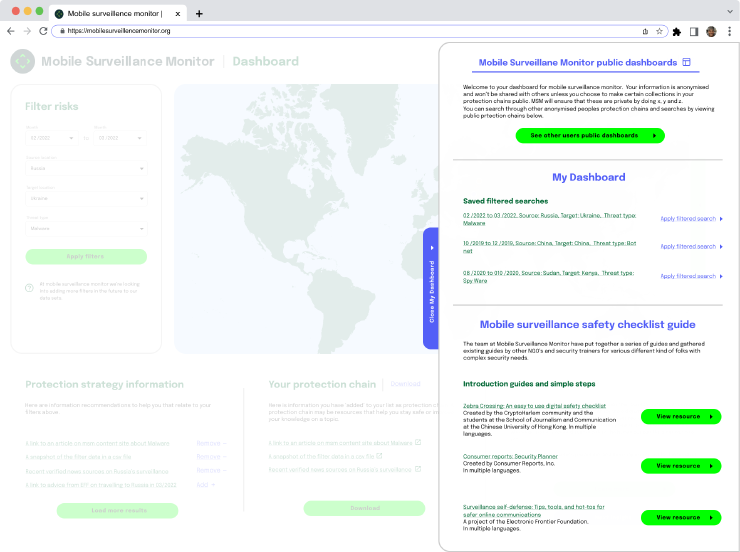
Phase 3 Design
We learned so much working with Gary on the Mobile Surveillance Monitor site; from responsible data practices doing high-risk user research to better informational design on a mapping application, this project was challenging and fulfilling for our team. We’re excited to see where MSM goes in the future.
Be sure to follow along by signing up for MSM data alerts and news!
Credits
OTF SUA Lab, Mobile Intelligence Alliance, Aldo Puicon