I was originally planning on continuing today the series I started last month, but it’s hard to pass up the opportunity to talk about Tuesday’s exciting WhatsApp’s update.
The new version of the messaging service’s apps now offers users a glimpse into a feature that has been quietly rolling out for months: end-to-end-encryption. A number of other groups have written about the update’s technical strengths and weaknesses – c.f. the EFF and ThreatPost, and WhatsApp’s own whitepaper – but I’d like to spend a moment on the updated user experience, and lessons that UX designers and developers can take from the decisions WhatsApp has made.
Users don’t have to take any action at all – it just works!
Always on for everyone
As long as both you and your messaging partner are running recent versions of the program, WhatsApp’s end-to-end-encryption is on by default, with no apparent way for the user to turn it off. This means that people don’t have to fuss with generating or exchanging cryptographic keys; it happens silently in the background. In fact, users don’t have to take any action at all – it just works!
Fredric Jacobs shares the error message he saw when his messaging partner was running an old version of the software (left) and the menu option to turn on notifications around encryption (right).
An exercise in tradeoffs
Of course, this seamlessness doesn’t come for free. Security enthusiasts are quick to point out limitations of this approach – in particular, that an application without mandatory key verification can be susceptible man-in-the-middle attacks. WhatsApp mitigates this limitation in two ways: by providing an optional key verification facility (which the EFF analyzes quite nicely) and by allowing users to opt-in to getting warning messages when their messaging partner’s key has changed (i.e., key-continuity detection).
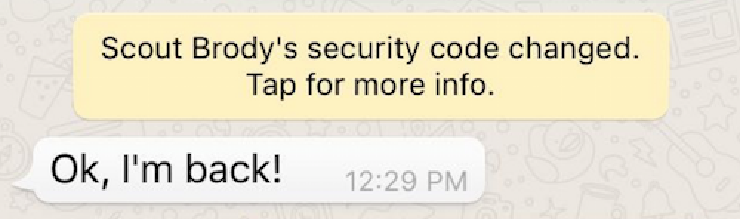 The message WhatsApp displays when the other user’s key has changed.
The message WhatsApp displays when the other user’s key has changed.
Noticing notifications
The current release of WhatsApp does not prompt users to opt-in to encryption-related notifications. The option to do so is a bit hidden in the Settings > Account > Security, but given how few options are in that menu, it’s reasonable to expect that someone poking around will discover it without too much trouble. I am curious whether WhatsApp did any user research before or during their design of this interface (which is pictured in Fred’s tweet above) to make it discoverable and appealing to users who aren’t necessarily looking for it. It should at least be easy to find for users who are seeking it out.
Designers working with security settings often have to be cautious about pushing users too hard to turn on things that won’t be useful to them. Time and again, intrusive security notifications have caused users to be frustrated to the point of turning off the security feature or switching to a less secure product. WhatsApp has done a good job on this front; in the absence of an attack, the notification is both rare (it should only occur when the other person has switched phones or uninstalled and reinstalled the app) and discrete once enabled.
However, I worry that it may be a little too discrete. When we were testing it, we actually managed to miss the inline message (pictured above) at first, even though we were explicitly looking for it! This may be because the chat thread wasn’t open when it appeared. Other messages came in after it, pushing it out of the user’s focus area, which is centered on the bottom of the screen. It took scrolling back up into the message history to see the inline message. Could an attacker exploit this focus issue with some users by intentionally sending a slew of distracting messages after signing on?
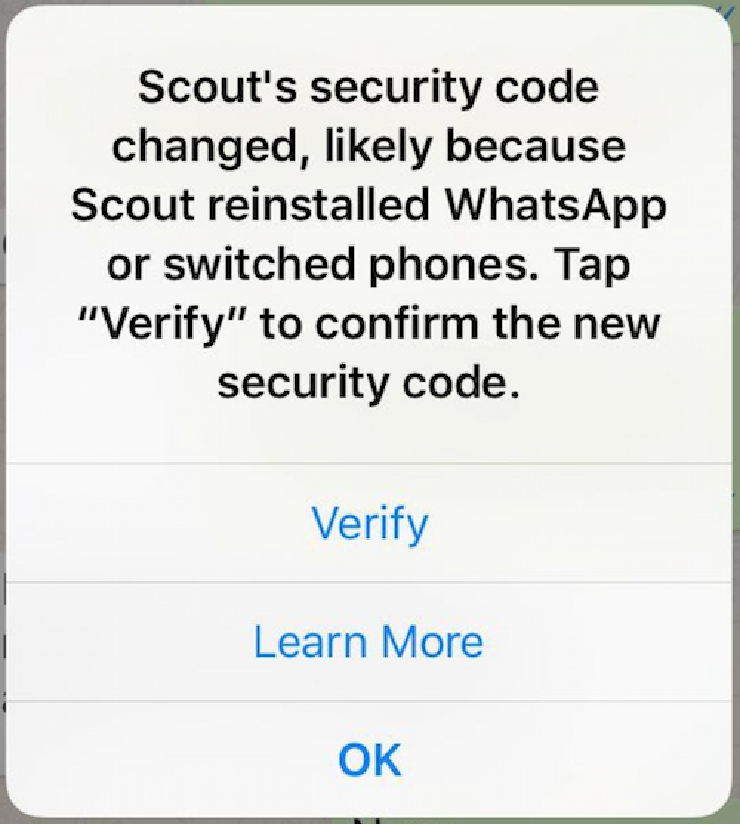 The dialog that appears when you tap the inline notification.
The dialog that appears when you tap the inline notification.
Furthermore, while the dialog that pops up when you “tap for more info” offers reasonable detail (and a “learn more” option), neither it nor the inline message itself help the user realize that “security code changed” means “your communication may be at risk”.
I understand that the cases where users are being attacked will be far, far outnumbered by the cases where their messaging partner has simply gotten a new phone. And it’s important to not overwhelm users with useless messages. At the same time, when the user chose to turn on these security notifications, they gave a strong signal that they were concerned about security. Perhaps the designers assumed that any user who turned this feature on would know what the warning meant? But if that’s the case, why use a term (“security code”) that is so friendly to security novices, rather than the one that experts are accustomed to (“key”)?
Here’s hoping: the importance of research and iteration
I am so pleased and impressed that WhatsApp has invested the time and energy necessary to release this feature that I am going assume (hope?) that this is just the first of several iterative improvements to this experience. Once they have a chance to look at how the feature has been received and get more data about how often people are engaging with it – likely through both in-app analytics and user research – they can work to make it even more discoverable and useful to users who want to learn more about their security status.
Here are some concrete suggestions that I would love to see explored.
- Are there ways to surface the notification feature to users who haven’t opened their account settings? This might itself be a one-time (or once-yearly) notification, ideally some time after the user has completed the initial setup flow so as not to get lost in dialog fatigue. Users could have the option to (1) go directly to their security settings, (2) be reminded to do so later, (3) or dismiss the suggestion permanently.
- Are there patterns of behavior that might indicate that the user is under attack, and be used to enable the notifications automatically? For example, sudden key changes by a number of the users’ contacts, or the user blocking a number of new contacts.
- Could the inline notification do more to indicate that the change in security code is worthy of investigation? Any solution would need to be coherent in the app’s visual design language, of course, but color or iconography could go a long way here.
- Is there some way to prevent users from missing the inline notification as we did in our experiments? The obvious choice would be to have the notification be a modal dialog the first time it appears for a given messaging partner (in addition to the inline message so the user could easily access it again if they accidentally dismissed it), but there are likely other options as well.
The perfect is the enemy of the good
All apps have room for improvement, and designing for both general users (who currently are unlikely to be subject to a MITM attack) and users at risk (who may be targeted by government-level attackers on a daily basis) is extremely hard to do. WhatsApp and Signal have pushed the envelope of UX design for cryptography to new territories, and have brought end-to-end encrypted messaging to over a billion people. We therefore applaud them for this accomplishment wholeheartedly, and enthusiastically await their future efforts in this realm!
Are there other design patterns that you have experienced that you think would work well in a context like WhatsApp? Have you tackled similar problems, and would you like to share your efforts with the public? Are you working on a software project and seeking help designing or researching similar experiences? Please get in touch!