In November, I had the opportunity to speak at the O’Reilly Security Conference in New York City.
I shared a number of insights that we have discussed here on the Simply Secure blog, including findings from Ame’s New York City study on privacy for mobile messaging.
I also sat down with Mac Slocum to talk about the importance of human factors in security (you can watch the interview here). Our conversation focused on security from a software developer’s perspective, advice on how to make tools more human-centric (e.g., talk to your actual users), and perspectives on big challenges in security (e.g., the Internet of Things).
However, most people aren’t security-focused software developers and aren’t intimately familiar with the technology that can help protect their online data. If you’re a UX expert and interested in learning more about security and privacy, your own digital footprint is a great place to start. Here are some concrete steps that you and your loved ones can take in the new year.
Steps for better privacy & security
As I have said before, security isn’t a binary property. Unlike Santa’s clear-cut naughty vs. nice list, the analysis of whether a system or app is secure has many shades of gray. Different people worry about different threats to their data; to use security terminology, everyone has their own threat model. To help you thoroughly consider the risks facing your data, the suggestions below dissect the kinds of threat each tip is meant to protect against.
 Two-factor authentication adds an extra layer of security to your account by requiring both your password and a second bit of information to sign in. Image from Google’s 2-step verification page.
Two-factor authentication adds an extra layer of security to your account by requiring both your password and a second bit of information to sign in. Image from Google’s 2-step verification page.
1. Use two-factor authentication
Whether it’s called two-step verification, login approvals, or login verification, two-factor authentication requires you to have both your password and a “second factor” before you can sign in to your account. In most cases, this second factor is a code generated on your mobile phone or sent to you as an SMS message, but some systems (including Google, Dropbox, and Github) support special USB devices or voice calls.
Protects against: Two-factor authentication prevents an attacker who has access to your password from gaining access to your account. You don’t have to be a famous person or have especially sensitive data to be a target of this kind of attack; most victims are everyday people. The vast majority of the online public would benefit from using two-factor authentication, especially for their email account, which can serve as a gateway to all their other accounts. If you are an activist or person facing dedicated attackers, it is even more essential that you sign up as many accounts as possible – and that you generate codes on your phone rather than receive them via SMS.
Words of caution: If you lose your phone or second factor, be prepared, as it may take up to a week or more to regain access to some accounts. Many services provide a set of single-use codes that you can print out and save for emergencies. Tucking them into your sock drawer is generally sufficient, but if you’re worried about targeted threats, you might consider writing them down by hand in a place that is harder for others to find.
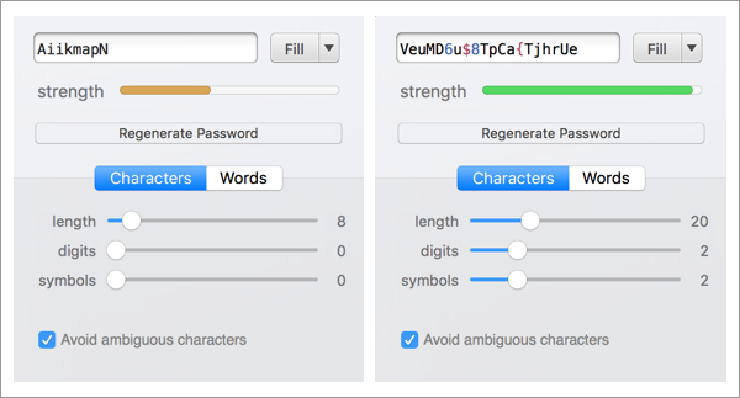 1Password is one of the more reputable password managers. In addition to following best practices around security (the company has collaborated in a number of third-party audits and documented the application’s security architecture publicly), it features handy details like a password generator with an engaging strength meter. Screenshot from 1Password 6.5.3.
1Password is one of the more reputable password managers. In addition to following best practices around security (the company has collaborated in a number of third-party audits and documented the application’s security architecture publicly), it features handy details like a password generator with an engaging strength meter. Screenshot from 1Password 6.5.3.
2. Use a password manager
I was a late convert to using a password manager. I thought that my own schemes for remembering passwords (and in some cases, reusing them for low-value sites) were sufficient. But at a certain point – after a big data breach became public or almost falling for a phishing attempt – I realized that I needed to admit my limitations. I now recommend 1Password to my friends and family. The default is their cloud-based version, which allows you to easily sync passwords across devices. As of this writing, they also offer versions for teams and for families as well as a non-synced edition for a flat license fee.
Protects against: Password managers make it easy for you to use long, complex passwords that are hard for attackers to crack. They also allow you to use a unique password for every site or application, which makes it impossible for an attacker to use a data breach on one platform to compromise your data on another. Finally, they make it less painful to change your password if a breach happens. They thus protect you from malicious attackers seeking to gain access to your personal information online through a compromised password. Again, most attacks against passwords aren’t targeted at famous people but common members of the population. Even your “low value” accounts, such as old social media profiles or email addresses, are worth protecting. Attackers often use them to try and extort money from your friends or to harvest personal information that they can then use in attacking a higher-value target.
Words of caution: Don’t use the first free password manager you come across. If you use a cloud-based password manager, try to avoid accessing it from a public computer that may be infected with spyware, such as one in an internet café or a hotel business center. If you are in a pinch and have to do so, change your vault password (the password that you use to unlock your password manager) as soon as you can get to your own computing device. If you are an activist who is worried that your government might be able to compel the password management company to share your data, consider using a version that isn’t based in the cloud. For example, since KeePass is an open-source password manager built by a decentralized, borderless community of developers, it would be hard to legally compel them to share your data.
3. Lock and encrypt your devices
When you turn on or wake up your computer or phone, do you use a password, PIN, pattern, or fingerprint to sign in? If not, even casual attackers can get access to your data when left alone with your device for just a few moments. While having to unlock your screen multiple times per day can be annoying, it is an important protective step for many people. Similarly, encrypting your device’s long term storage (e.g., its hard drive) prevents slightly more dedicated attackers from stealing your data by plugging it into their computer and scanning it. This method can allow them to access even devices that have a screen lock.
Protects against: Screen locks prevent would-be attackers from getting into your device when they have physical access to it. This includes cases where you forgot your phone in a taxi or where your computer was stolen from your home. It may also include cases where your device is in a locked environment that others have access to, such as a locked hotel room, or during targeted searches such as at international border crossings. Encryption also protects against more dedicated attacks by people who have physical access to your device for an extended period of time. With the important caveat noted below, both device encryption and screen locks pose very little downside and significant upside.
Words of caution: If you encrypt your device, it’s important to write down the password, PIN, or pattern you use to unlock it in a safe place. Losing access to your unlock code means that you permanently lose access to the data on the device. If you are worried about targeted in-person threats, screen locks that employ codes or passphrases may be a better choice than fingerprints, as there’s evidence that biometric readers can be fooled.
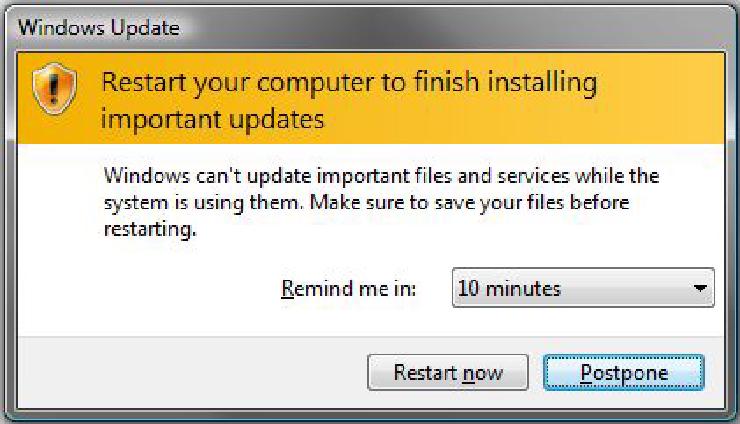 It’s easy to ignore update notifications when you’re busy. Don’t postpone them for too long! Screenshot by mynetx, CC BY-SA 2.0.
It’s easy to ignore update notifications when you’re busy. Don’t postpone them for too long! Screenshot by mynetx, CC BY-SA 2.0.
4. Install updates
Writing software is a human process, which means that all software can have flaws. Software updates decrease the likelihood of your data falling prey to known vulnerabilities. Just as a homeowner regularly changes the batteries on a smoke detector and cleans out the gutters, it’s important to make sure the devices and software you rely on have up-to-date software and firmware. This includes your phone and computer operating systems, your web browser, and your apps. It also includes smart TVs, game consoles, and routers. If you’re not sure how to tell whether something is up to date, a web search for “check to see whether [product name] is up to date” often yields good instructions.
Protects against: Software updates protect against digital attacks that target known vulnerabilities. These can be manual, such as a malicious hacker trying to steal your data, or automated attacks, including worms that jump from device to device. Once again, these attacks aren’t designed just for famous or powerful people but anyone who has devices on the internet.
Words of caution: Make sure that you’re using the official channel to get authentic software updates. Don’t download updates from links that you see in emails, which may be phishing attacks, or in online advertisements, which may be vectors for malware infection.
More resources
The beginning of a new year is always a great time to pick up new habits and new knowledge. For some additional guides on getting started with privacy- and security-conscious practices, check out Martin Shelton’s Medium stream. To learn more about the big picture of protecting your data from surveillance, which can be especially important if you’re an activist or someone who might be subject to particular scrutiny by your government, check out EFF’s site on surveillance self-defense. Many of its resources are also useful for everyday people, too, such as its overview animation on password managers or its tutorial on encrypting your iPhone.
Are you a designer or UX researcher interested in learning more and integrating a greater awareness of privacy and security into your practice? Join our Slack community!